Context:
A number of reports on Pegasus Spyware in India indicate that at least 1,000 Indian phone numbers are in a list of potential targets of surveillance using the Pegasus spyware. An Israeli company, the NSO Group, sells the Pegasus spyware to “vetted governments”.
The evidence is strong that Indian citizens were indeed targets of a vicious and uncivil surveillance campaign by a government entity, Indian or foreign.
Relevance:
GS-III: Internal Security Challenges (Basics of Cyber Security; Role of media and social networking sites in internal security challenges; Internal security challenges through communication networks), GS-II: Polity and Governance (Constitutional Provisions, Fundamental Rights, Important Judgements)
Dimensions of the Article:
- About the Pegasus Project
- How dangerously compromising is Pegasus?
- What is a spyware and what are other similar types of Cyber Attacks?
- Pegasus in the news in the past
- About the Pegasus Attacks in India
- Issues in the past regarding Government’s surveillance
- Legislations on Surveillance
- K.S. Puttaswamy judgment, 2017 regarding Surveillance
- Various recommendations in the past regarding Surveillance
About the Pegasus Project
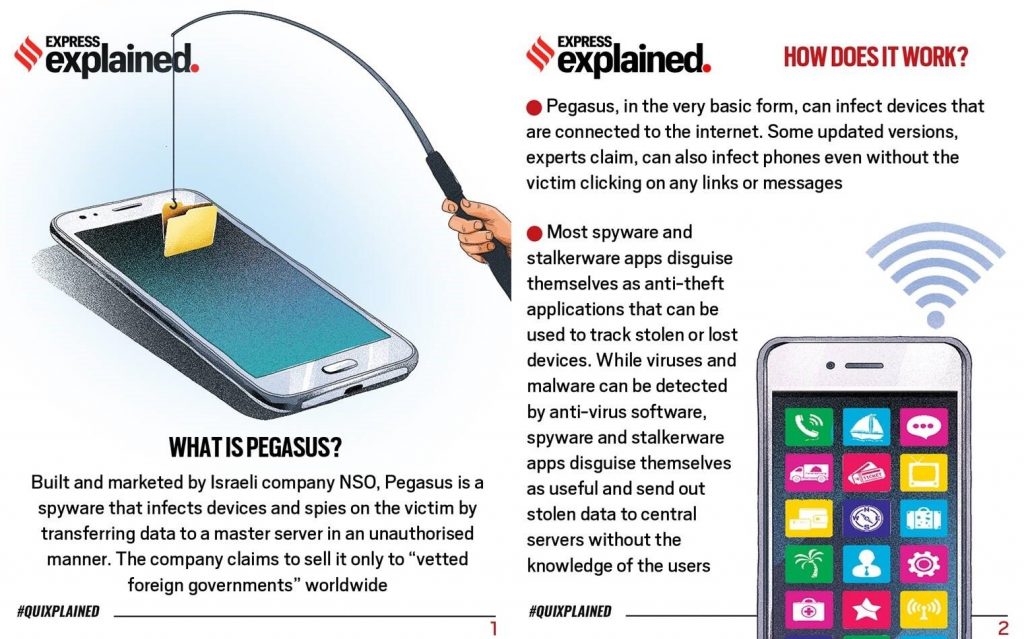
- Pegasus is a type of malware classified as a spyware. Pegasus enables law enforcement and intelligence agencies to remotely and covertly extract” data “from virtually any mobile devices”
- The Spyware Pegasus can gain access to devices without the knowledge of users. After this, it can gather personal information and relay it back to whoever is using the software to spy.
- A zero-click attack helps spyware like Pegasus gain control over a device without human interaction or human error. Pegasus can infect a device without the target’s engagement or knowledge. So, all awareness about how to avoid a phishing attack or which links not to click are pointless.
- The Israeli firm NSO Group (set up in 2010) developed the Pegasus spyware. Since then, NSO’s attack capabilities have become more advanced.
How dangerously compromising is Pegasus?
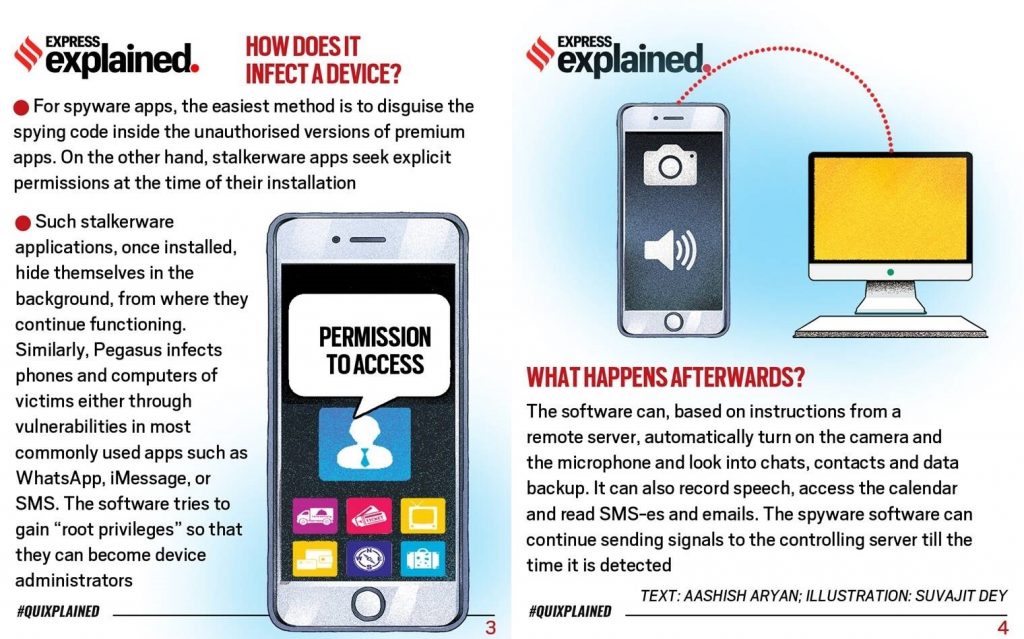
- Upon installation, Pegasus contacts the attacker’s command and control (C&C) servers to receive and execute instructions and send back the target’s private data. This data can include passwords, contact lists, text messages, and live voice calls (even those via end-to-end-encrypted messaging apps).
- The attacker can control the phone’s camera and microphone, and use the GPS function to track a target.
- To avoid extensive bandwidth consumption that may alert a target, Pegasus sends only scheduled updates to a C&C server.
- The spyware can evade forensic analysis and avoid detection by anti-virus software. Also, the attacker can remove and deactivate the spyware, when and if necessary.
What is a spyware (Like Pegasus Spyware in India) and what are other similar types of Cyber Attacks?
What is Malware?
- Malware is short for malicious software. Malware is a catch-all term for various softwares including viruses, adware, spyware, browser hijacking software, and fake security software.
- Ransomware, Spyware, Worms, viruses, and Trojans are all varieties of malware.
Types of Malware
- Viruses which are the most commonly-known form of malware and potentially the most destructive. They can do anything from erasing the data on your computer to hijacking your computer to attack other systems. Viruses can also send spam, or host and share illegal content.
- Worm is a type of malware that spreads copies of itself from computer to computer. Additionally, it can replicate itself without any human interaction. Also, it does not need to attach itself to a software program in order to cause damage.
- Trojan is a type of malware that is often disguised as legitimate software to be used by cyber-thieves and hackers trying to gain access to systems.
- Spyware collects your personal information and passes it on to interested third parties without your knowledge or consent. Spywares can also install Trojan viruses.
- Ransomware is malware that employs encryption to hold a victim’s information at ransom.
- Adware displays pop-up advertisements when you are online.
- Fake security software poses as legitimate software to trick you into opening your system to further infection, providing personal information, or paying for unnecessary or even damaging “clean ups”.
- Browser hijacking software changes your browser settings (such as your home page and toolbars), displays pop-up ads and creates new desktop shortcuts. Additionally, it can also relay your personal preferences to interested third parties.
Pegasus Spyware in India in the news in the past
- Researchers discovered the earliest version of Pegasus in 2016. This version infected phones through what is called spear-phishing – text messages or emails that trick a target into clicking on a malicious link.
- In 2019, WhatsApp blamed the NSO Group for exploiting a vulnerability in its video-calling feature which secretly transmitted malicious code in an effort to infect the victim’s phone with spyware without the person even having to answer the call.
- In 2020, a report showed government operatives used Pegasus to hack phones of employees at Al Jazeera and Al Araby.
About the Recent Pegasus Spyware Attacks in India
- Human Rights activists, journalists and lawyers around the world have been targeted with phone malware sold to authoritarian governments by an Israeli surveillance firm. Indian ministers, government officials and opposition leaders also figure in the list.
- In India, several opposition leaders including Rahul Gandhi were on the leaked potential targets’ list.
- Smartphones of Politicians, Journalists were hacked for gathering confidential information.
- This is the first time in the history of this country that all pillars of our democracy — judiciary, parliamentarians, media, executives and ministers — have been spied upon.
- The Indian government has denied any wrong doing or carrying out any unauthorised surveillance. However, the government has not confirmed or denied whether it has purchased or deployed Pegasus spyware.
Issues in the past regarding Government’s surveillance
- In 2012 in Himachal Pradesh, the new government raided police agencies and recovered over a lakh phone conversations of over a thousand people, mainly political members, and many senior police officials, including the Director General of Police (DGP), who is legally responsible for conducting phone taps in the State.
- In 2013, India’s current Home Minister Amit Shah was embroiled in a controversy dubbed “Snoopgate”, with phone recordings alleged to be of him speaking to the head of an anti-terrorism unit to conduct covert surveillance without any legal basis (as there was no order signed by the State’s Home Secretary which is a legal necessity for a phone tap).
- The UPA government in 2009 said that the CBDT had placed a PR professional, under surveillance due to fears of her being a foreign spy. Later on, the CBDT did not prosecute the person.
Such examples of unlawful surveillance which seem to be for political and personal gain are antithetical to the basic creed of democracy. Consequently, they also bring up the need for ensuring that the surveillance is necessary and proportionate.
Legislations on Surveillance
- The laws authorising interception and monitoring of communications are:
- Section 92 of the Criminal Procedure Code (CrPC)
- Rule 419A of the Telegraph Rules, and
- The rules under Sections 69 and 69B of the IT Act
Who can conduct Surveillance?
A limited number of agencies are provided powers to intercept and monitor.
- In 2014, the Ministry of Home Affairs told Parliament that nine central agencies and the DGPs of all States and Delhi were empowered to conduct interception under the Indian Telegraph Act.
- In 2018, 9 central agencies and 1 State agency were authorised to conduct intercepts under Section 69 of the IT Act.
- The Intelligence Organisations Act, which restricts the civil liberties of intelligence agency employees, only lists four agencies. However, the RTI Act lists 22 agencies as “intelligence and security organisations established by the central government” that are exempt from the RTI Act.
K.S. Puttaswamy judgment, 2017 regarding Surveillance
- The K.S. Puttaswamy judgment, 2017, made it clear that any invasion of privacy could only be justified if it satisfied three tests:
- The restriction must be by law;
- It must be necessary (only if other means are not available) and proportionate (only as much as needed);
- It must promote a legitimate state interest (e.g., national security).
- The judgement held that privacy concerns in this day and age of technology can arise from both the state as well as non-state entities. As such, a claim of violation of privacy lies against both of them.
- The Court also held that informational privacy in the age of the internet is not an absolute right and when an individual exercises his right to control over his data, it may lead to the violation of his privacy to a considerable extent.
- It was also laid down that the ambit of Article 21 is ever-expanding due to the agreement over the years among the Supreme Court judges. A plethora of rights have been added to Article 21 as a result.
- The court stated that Right to Privacy is an inherent and integral part of Part III of the Constitution that guarantees fundamental rights. The conflict in this area mainly arises between an individual’s right to privacy and the legitimate aim of the government to implement its policies. Thus, we need to maintain a balance while doing the same.
Various recommendations in the past regarding Surveillance
- In 2010, then Vice-President called for a legislative basis for India’s agencies and the creation of a standing committee of Parliament on intelligence to ensure that they remain accountable and respectful of civil liberties.
- The Cabinet Secretary in a note on surveillance in 2011 held that the Central Board of Direct Taxes having interception powers was a continuing violation of a 1975 Supreme Court judgment on the Telegraph Act.
- In 2013, the Ministry of Defence-funded think-tank published a report which recommended that the intelligence agencies in India must be provided a legal framework for their existence and functioning; their functioning must be under Parliamentary oversight and scrutiny.
- In 2018, the Srikrishna Committee on data protection noted that post the K.S. Puttaswamy judgment, most of India’s intelligence agencies are “potentially unconstitutional”. This is because they are not constituted under a statute passed by Parliament — the National Investigation Agency being an exception.
Click Here to read about Cyber Attacks, International legislative responses and cooperation regarding cybercrime and more
-Source: The Hindu, Indian Express




