CONTENTS
- Sixth Anniversary of the Minamata Convention
- Gene edited low-pungent mustard
- Nutrition and Tuberculosis (TB) Prevention
- Acoustic Side Channel Attack
- Kashmir stag
- TAPAS UAV
- Madan Lal Dhingra
Sixth Anniversary of the Minamata Convention
Context:
The sixth anniversary of the Minamata Convention on Mercury is a reminder of global efforts to combat the toxic effects of mercury. On this occasion, the United Nations Environment Programme (UNEP) reflects on the ongoing campaign to eradicate the use of mercury in small-scale gold mining.
Relevance:
GS III: Environment and Ecology
Dimensions of the Article:
- About the Minamata Convention
- Mercury Pollution: Sources, Impact, and Applications
- Path Forward to Address Mercury Pollution
About the Minamata Convention:
The Minamata Convention stands as a worldwide accord designed to safeguard human well-being and the environment against the detrimental impacts of mercury and its derivatives.
Origins and Agreement:
- The Convention’s formulation was finalized during the fifth session of the Intergovernmental Negotiating Committee, held in Geneva, Switzerland in 2013.
Mitigating Anthropogenic Impact:
- A pivotal obligation under the Convention involves the regulation of human-induced discharges of mercury across its complete life cycle.
Mercury Pollution: Sources, Impact, and Applications
About Mercury:
- Mercury is a naturally occurring element found in the Earth’s crust and considered a significant public health concern by WHO.
Major Applications:
- Mercury is used in thermometers, barometers, and mercury-wetted switches due to its thermal expansion and electrical conductivity.
- It’s employed in chemical processes, gold mining, and electronics manufacturing.
Sources of Mercury Pollution:
- Natural Sources: Volcanic eruptions and erosion release mercury into the environment.
- Anthropogenic Sources: Activities like Artisanal and Small-Scale Gold Mining (ASGM), industrial processes, and improper e-waste disposal contribute to mercury pollution.
ASGM and Mercury Emissions:
- ASGM employs mercury to extract gold from ores, leading to mercury emissions during gold extraction.
- Artisanal gold mining contributes significantly to global mercury pollution, accounting for 37% of emissions.
Industrial Processes and Waste Disposal:
- Industries such as chlorine production, cement manufacturing, and waste incineration release mercury.
- E-waste containing mercury, like fluorescent bulbs and batteries, contributes to environmental pollution.
Impact on Health and Environment:
- Methylmercury, accumulated in aquatic organisms like fish, poses health risks to humans who consume contaminated fish.
- Exposure to methylmercury can lead to Minamata disease, characterized by sensory impairment, tremors, and sensory deficits.
- Mercury pollution arises from both natural sources and human activities, affecting ecosystems and human health alike.
Path Forward to Address Mercury Pollution
Innovative Mercury Removal:
- Develop and implement mercury-removal filters in industrial emissions, wastewater treatment, and consumer products.
- These filters can selectively capture mercury particles from air and water streams, reducing emissions.
Phytoremediation:
- Utilize phytoremediation, where plants absorb and accumulate mercury from soil, water, or sediments.
- Harvest and dispose of these plants to effectively remove mercury from the environment.
Global Implementation of planetGOLD:
- Collaborate with the UNEP-led planetGOLD program to eliminate mercury from artisanal gold mining and enhance worker safety.
- This initiative aligns with the Minamata Convention’s goals and offers financial and technical support to transition miners away from mercury use.
Mercury-Free Processing Plants:
- Establish mercury-free processing plants as exemplified by Burkina Faso’s model under planetGOLD.
- Demonstrate successful transitions away from mercury use in gold mining operations.
-Source: The Hindu
Gene Edited Low-Pungent Mustard
Context:
Recently, Indian scientists developed the first ever Gene edited low-pungent mustard that is pest and disease-resistant.
Relevance:
GS III: Science and Technology
Dimensions of the Article:
- Issues with Mustard Seeds
- Gene Editing Breakthrough
- Impact
Issues with Mustard Seeds:
- Rapeseed-mustard is a significant oilseed crop in India.
- Mustard seeds contain high levels of glucosinolates, compounds responsible for pungency in oil and meal.
- Glucosinolates make rapeseed meal unpalatable to animals and can cause health issues like goiter in livestock.
Gene Editing Breakthrough:
- Researchers focused on glucosinolate transporter (GTR) genes responsible for glucosinolate accumulation in mustard seeds.
- 12 GTR genes categorized into GTR1 and GTR2 classes play a role in transporting glucosinolates to seeds.
- Using CRISPR/Cas9 gene-editing tool, 10 out of 12 GTR genes in the ‘Varuna’ mustard variety were edited.
- This disrupted the functioning of proteins responsible for transporting glucosinolates to seeds.
Outcome and Benefits:
- By editing GTR genes, glucosinolate content in seeds was reduced, matching canola-quality rapeseed.
- Mustard lines with lower glucosinolate content were developed, providing oil and meal similar to canola.
- The new mustard lines are transgene-free, without foreign genes, ensuring they are non-genetically modified (GM).
Impact:
- Gene-edited mustard holds potential to address pungency and palatability issues in rapeseed meal.
- Livestock feed intake can be improved, avoiding health problems and reducing the need for mixing with fodder grass.
- This breakthrough can contribute to enhancing the quality and utility of domestically grown oilseeds in India.
-Source: Indian Express
Nutrition and Tuberculosis (TB) Prevention
Context:
Recently, two studies conducted by the Indian Council of Medical Research (ICMR) and published in prestigious journals such as The Lancet and The Lancet Global Health, have unveiled a pivotal connection between nutrition and tuberculosis (TB) prevention.
Relevance:
GS II: Health
Dimensions of the Article:
- Key Findings from the Studies on Nutrient-Dense Food for TB Patients
- Tuberculosis
Key Findings from the Studies on Nutrient-Dense Food for TB Patients
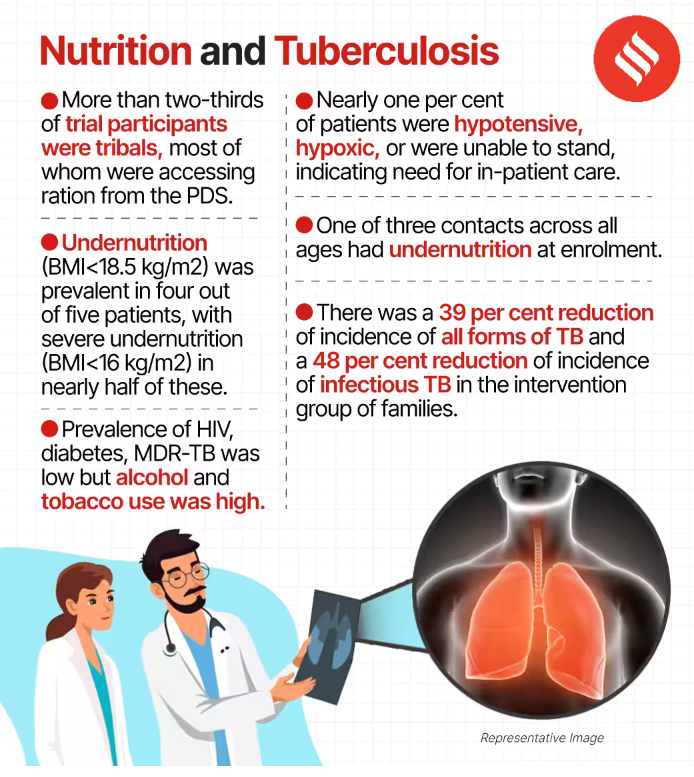
- Participant Demographics: The studies involved a total of 5,621 participants who received nutrient-dense food for a year, and 4,724 participants who received regular food parcels with no additional nutrition.
- TB Incidence Reduction: The intervention group receiving nutrient-dense food experienced a significant reduction in tuberculosis (TB) incidence, with a 39% lower incidence compared to the control group.
- Impact of Weight Gain: In severely malnourished TB patients in Jharkhand, weight gain was associated with decreased risks of tuberculosis mortality.
- Effect of Weight Gain: A 1% increase in weight was linked to a 13% reduction in the instantaneous risk of death, while a 5% increase in weight led to a substantial 61% reduction in this risk.
- Study Sample: The study focused on 2,800 severely malnourished TB patients in Jharkhand, where 4 out of 5 patients were found to have undernutrition.
- Nutritional Support Duration: Nutritional support was provided for six months to individuals responding to TB drugs, while those with multidrug-resistant tuberculosis received support for 12 months.
- Early Weight Gain: Patients who experienced weight gain during the first two months of treatment had a significantly lower risk of TB mortality, with a 60% reduction.
- Treatment Success: Patients receiving nutrient-dense food showed higher rates of treatment success, better weight gain, and lower rates of weight loss during follow-up periods.
Tuberculosis
- TB remains the world’s deadliest infectious killer.
- Each day, over 4000 people lose their lives to TB and close to 30,000 people fall ill with this preventable and curable disease
- TB is caused by bacteria (Mycobacterium tuberculosis) that most often affect the lungs.
- Transmission: TB is spread from person to person through the air. When people with TB cough, sneeze or spit, they propel the TB germs into the air.
- Symptoms: Cough with sputum and blood at times, chest pains, weakness, weight loss, fever and night sweats.
- Treatment: TB is a treatable and curable disease. It is treated with a standard 6 month course of 4 antimicrobial drugs that are provided with information, supervision and support to the patient by a health worker or trained volunteer.
- Anti-TB medicines have been used for decades and strains that are resistant to 1 or more of the medicines have been documented in every country surveyed.
- Multidrug-resistant tuberculosis (MDR-TB) is a form of TB caused by bacteria that do not respond to isoniazid and rifampicin, the 2 most powerful, first-line anti-TB drugs. MDR-TB is treatable and curable by using second-line drugs.
- Extensively drug-resistant TB (XDR-TB) is a more serious form of MDR-TB caused by bacteria that do not respond to the most effective second-line anti-TB drugs, often leaving patients without any further treatment options
-Source: The Hindu
Acoustic Side Channel Attack
Context:
A research paper titled “A Practical Deep Learning-Based Acoustic Side Channel Attack on Keyboards”, revealed that Artificial Intelligence (AI) can be used to decode passwords by analysing the sound produced by keystrokes.
Relevance:
GS III: Science and Technology
Dimensions of the Article:
- Acoustic Side Channel Attack (ASCA)
- Side Channel Attacks (SCAs)
Acoustic Side Channel Attack (ASCA)
- Acoustic Side Channel Attack (ASCA) is a novel hacking technique that exploits the sounds generated by typing on a keyboard to decipher the pressed keys.
- The distinct audio signatures produced by each keypress are analyzed to deduce the specific letters and numbers being typed.
Methodology:
- Hackers leverage advanced tools to capture and analyze audio recordings from various sources, including Zoom video conferencing calls and smartphone microphones.
- These audio recordings are processed using algorithms and machine learning models to decode the keyboard inputs.
Research Findings:
- A study delved into ASCA attacks using different audio sources and machine learning techniques.
- Researchers demonstrated that training a deep learning model with audio data from nearby smartphones led to an impressive accuracy of 95% in recognizing typed keystrokes.
- The model achieved exceptional accuracy with minimal training data on MacBook Pro keyboards.
Implications and Security Concerns:
- The use of ASCA introduces significant security concerns as it can potentially expose sensitive information.
- This technique could compromise passwords, confidential messages, and other private data, thereby posing a threat to personal privacy and data security.
Advancements in Hacking Techniques:
- ASCA exemplifies how hackers are constantly evolving their methods to exploit unique vulnerabilities.
- Traditional security measures might not be sufficient to counter such innovative techniques that exploit non-traditional attack vectors.
Protection and Prevention:
- To mitigate the risks associated with ASCA attacks, individuals and organizations should consider adopting:
- Noise-reducing measures: Reducing the audio footprint of keystrokes can make it harder for attackers to gather meaningful data.
- Advanced cybersecurity tools: Implementing advanced security solutions that detect and prevent unconventional attack methods.
- User awareness: Educating users about the potential risks of audio-based attacks and the importance of secure typing environments.
Side Channel Attacks (SCAs)
- Side Channel Attacks (SCAs) are sophisticated hacking techniques that exploit unintended information leakage from auxiliary systems associated with cryptographic algorithms.
- Unlike traditional attacks that target algorithm weaknesses, SCAs focus on analyzing auxiliary signals to infer sensitive data.
Attack Methodology:
- SCAs target various devices, including electronic systems, by analyzing signals emitted during cryptographic operations.
- Auxiliary Signals: These attacks leverage unintentional signals, such as electromagnetic radiation, power consumption, acoustic emissions (sound), or even temperature fluctuations.
Types of Side Channel Attacks:
Electromagnetic Attacks:
- Capture electromagnetic emissions from electronic components during computations.
- Analyze these emissions to infer cryptographic keys or other sensitive data.
Power Analysis Attacks:
- Monitor the power consumption of a device during cryptographic operations.
- Variations in power consumption can provide insights into the internal computations and, consequently, the encryption keys.
Acoustic Attacks:
- Capture sounds produced by devices during operations (e.g., typing on a keyboard, printing).
- Analyze the audio signals to decipher patterns that reveal sensitive information.
Timing Attacks:
- Exploit variations in execution time of cryptographic operations.
- Analyze the time taken to perform specific tasks to infer cryptographic keys.
Implications:
- SCAs are stealthy and often go unnoticed since they don’t directly attack the cryptographic algorithms.
- Attackers can recover encryption keys or sensitive data, compromising the security and confidentiality of a system.
Mitigation:
- Developing countermeasures against SCAs is challenging due to the wide range of potential leakage sources.
- Implementing techniques like randomizing execution times, using noise to mask signals, or using hardware-based protections can help mitigate SCAs.
Significance:
- SCAs highlight the importance of considering all potential sources of information leakage when designing secure systems.
- Security experts need to continually evolve their strategies to prevent sophisticated attacks that exploit unconventional vulnerabilities.
-Source: The Hindu
Kashmir Stag
Context:
After two years, the unique Kashmir stag (Hangul) the state animal of Jammu and Kashmir, has again shown a marginal increase in its population.

Relevance:
GS III: Species in News
Dimensions of the Article:
- Kashmir Stag (Hangul)
- Dachigam National Park: Key Highlights
Kashmir Stag (Hangul):
- Commonly Known as Hangul: The Kashmir stag, also known as Hangul, is a subspecies of Central Asian red deer that is endemic to the region of Kashmir and its surroundings.
- Habitat: These deer are found in the dense riverine forests of the high valleys and mountains in regions of Jammu and Kashmir and northern Himachal Pradesh.
- Protected Area: The Dachigam National Park in Kashmir serves as a significant habitat for the Hangul, providing protection and preservation for this species.
- Population: While their population is limited, a small group of Hangul has also been observed in the Overa-Aru Wildlife Sanctuary in south Kashmir.
Conservation Status:
- IUCN Status: The Hangul is classified as “Critically Endangered” by the International Union for Conservation of Nature (IUCN), highlighting its high risk of extinction.
- CITES Listing: It is listed under Appendix I of the Convention on International Trade in Endangered Species of Wild Fauna and Flora (CITES), offering the highest level of protection against trade.
Dachigam National Park: Key Highlights
- Diverse Terrain: The park’s true beauty is showcased through its deep valleys, rugged rock formations, steep forested slopes, and expansive alpine meadows.
- Altitude Variation: Situated in a mountainous region, Dachigam National Park experiences a significant variation in altitude, ranging from 1600 meters to 4200 meters above sea level.
- Distinct Regions: This altitude diversity divides the park into two distinct regions: the upper region and the lower region, each with unique ecological features.
- Flora Abundance: The park boasts a rich flora, including various species such as Wild Cherry, Pear, Plum, Peach, Apple, Apricot, Walnut, Chestnut, Oak, and Willow.
- Varied Fauna: Dachigam National Park is home to a diverse range of wildlife:
- Hangul (Kashmir Stag): This park is a crucial habitat for the endangered Hangul, also known as the Kashmir Stag.
- Musk Deer, Leopards, and More: Other residents include Musk deer, Brown Bears, Leopards, Jungle Cats, Himalayan black bears, and several species of wild goats like markhor and ibex.
-Source: The Hindu
TAPAS UAV
Context:
Recently, a Tapas unmanned aerial vehicle (UAV) of the Defence Research and Development Organisation (DRDO) crashed in agriculture fields near a village in Karnataka’s Chitradurga.
Relevance:
GS III: Science and Technology
Tactical Airborne Platform for Aerial Surveillance-Beyond Horizon-201 or Tapas BH-201
Long-Endurance Unmanned Aerial Vehicle: TAPAS UAV, previously known as Rustom-II, is an advanced long-endurance unmanned aerial vehicle designed for aerial surveillance and intelligence gathering.
Impressive Specifications:
- Wingspan: With a substantial wingspan of 20.6 meters, TAPAS UAV boasts a considerable aerial presence.
- Speed: It can achieve a maximum speed of 225 kmph, allowing for efficient coverage of areas of interest.
- Range: The drone offers extended coverage with a range of over 250 km via the C Band frequency data link and 1000+ km via SATCOM using Kᵤ Band frequency and the GAGAN system.
High Altitude and Endurance:
- The medium-altitude, long-endurance design permits TAPAS UAV to reach altitudes of up to 28,000 feet.
- The drone’s flight endurance is noteworthy, with a range of over 18 hours, enabling it to operate for extended periods.
Technological Advancements:
- Developed by the Aeronautical Development Establishment, TAPAS UAV leverages cutting-edge technology for its construction and operation.
- The real-time data collection and transmission capabilities provide crucial intelligence for informed decision-making.
Transportable and Versatile:
- TAPAS UAV’s compact and lightweight design ensures easy transportation and deployment, even in remote and challenging environments.
Operational Success:
- The drone has successfully completed numerous flights, accumulating valuable operational experience.
- With more than 180 flights under its belt, TAPAS UAV has demonstrated its reliability and capabilities.
Showcasing at Aero India 2023:
- TAPAS UAV will participate in Aero India 2023, where it will conduct live-streaming aerial and static displays.
- The event provides an opportunity to showcase the drone’s features and potential to a wider audience.
-Source: Hindustan Times
Madan Lal Dhingra
Context:
On the 114th death anniversary of Madan Lal Dhingra, a massive memorial was inaugurated in Amritsar, where he hailed from.

Relevance:
GS I: History
Madan Lal Dhingra: Indian Revolutionary Freedom Fighter
- Early Life: Madan Lal Dhingra was born on February 18, 1883, in Amritsar, India.
- Education: After receiving his early education in Amritsar, Dhingra went to England for higher studies. He enrolled at University College, London, where he pursued engineering.
- Involvement in Independence Movement: While studying in England, Dhingra became deeply engaged in the activities of the Indian independence movement. He associated with prominent revolutionaries such as Vinayak Damodar Savarkar and Shyamji Krishna Varma.
- Curzon Wyllie’s Assassination: On July 1, 1909, Dhingra assassinated Sir William Hutt Curzon Wyllie, a retired British Indian Army officer and official, during a public meeting at London’s Imperial Institute.
- Motivation for the Assassination: During his trial, Dhingra claimed that he murdered Curzon Wyllie as a patriotic act and in retaliation for the British Government’s brutal treatment of Indians in India.
- Trial and Sentencing: Dhingra was found guilty of the assassination and was sentenced to death.
- Execution: At the young age of 24, Madan Lal Dhingra was executed by hanging on August 17, 1909.
- Family Disownment: Due to his anti-British stance, Dhingra was disowned by his family. Even after his death, his family refused to claim his body.
-Source: Indian Express




