CONTENTS
- Here is why the electoral bonds scheme must go
- The rising tensions in the Balkans
- Pegasus spyware
- Economic recovery is yet to attain durability, says ICRA
- Silver Line project
- Miss Kerala
- Swamp Deer
Here Is why the Electoral Bonds Scheme Must Go
Context:
Electoral bonds violates the basic tenets of India’s democracy by keeping the knowledge of the ‘right to know’ from citizens and voters
Relevance:
GS-II: Polity and Governance (Governance and Government Policies)
Dimensions of the Article:
- What are Electoral Bonds?
- Points in the Plea against the Electoral Bonds scheme
- A blow against democracy
- Government’s response defending the Electoral Bonds scheme
- Way forward
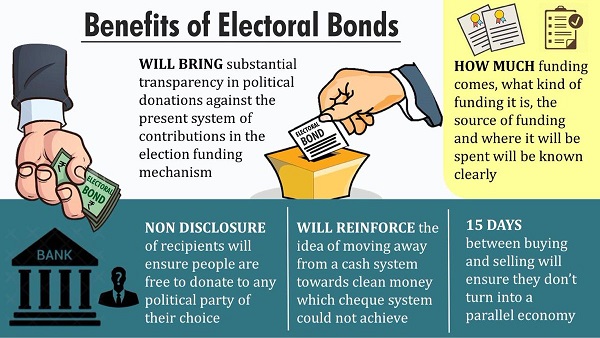
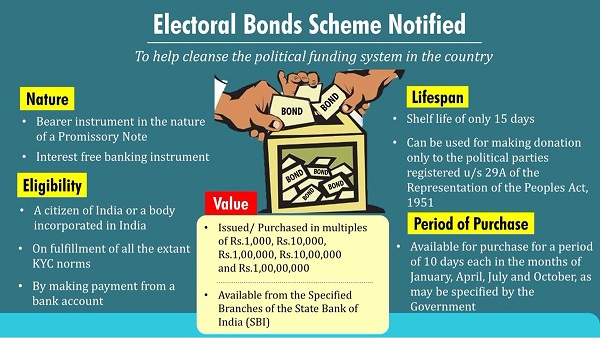
What are Electoral Bonds?
- An electoral bond is like a promissory note that can be bought by any Indian citizen or company incorporated in India from select branches of State Bank of India.
- The citizen or corporate can then donate the same to any eligible political party of his/her choice.
- The bonds are similar to bank notes that are payable to the bearer on demand and are free of interest.
- An individual or party will be allowed to purchase these bonds digitally or through cheque.
Points in the Plea against the Electoral Bonds scheme
- The Reserve Bank of India (RBI) and the Election Commission had both said the sale of electoral bonds had become an avenue for shell corporations and entities to park illicit money and even proceeds of bribes with political parties.
- Data obtained through RTI has shown that illegal sale windows have been opened in the past to benefit certain political parties. There is a serious apprehension that any further sale of electoral bonds before the upcoming State elections in West Bengal, Tamil Nadu, Kerala and Assam would further increase illegal and illicit funding of political parties through shell companies.
- The plea said that the Electoral Bonds scheme “opened doors to unlimited political donations, even from foreign companies, thereby legitimising electoral corruption at a huge scale, while at the same time ensuring complete non-transparency in political funding”.
A blow against democracy
- If democracy means anything, it must mean this: when citizens cast their votes for the people who will represent them in Parliament, they have the right to do so on the basis of full and complete information.
- And there is no piece of information more important than the knowledge of who funds political parties.
- Across democratic societies, and through time, it has been proven beyond doubt that money is the most effective way of buying policy, of engaging in regulatory capture, and of skewing the playing field in one’s own favour.
- The Indian Supreme Court has long held — and rightly so — that the “right to know”, especially in the context of elections, is an integral part of the right to freedom of expression under the Indian Constitution.
- It is equally important that if a democracy is to thrive, the role of money in influencing politics ought to be limited.
- The electoral bonds scheme, however, removes all pre-existing limits on political donations, and effectively allows well-resourced corporations to buy politicians by paying immense sums of money. This defeats the entire purpose of democracy.
- However, not only do electoral bonds violate basic democratic principles by allowing limitless and anonymous donations to political parties, they do so asymmetrically.
- Since the donations are routed through the State Bank of India, it is possible for the Government to find out who is donating to which party, but not for the political opposition to know.
- This, in turn, means that every donor is aware that the central government can trace their donations back to them.
- By keeping this knowledge from citizens and voters, the electoral bonds scheme violates fundamental tenets of our democracy.
Government’s response defending the Electoral Bonds scheme
- The Government said that the Electoral Bond Scheme allowed anonymity to political donors to protect them from “political victimisation”. The earlier system of cash donations had raised a “concern among the donors that, with their identity revealed, there would be competitive pressure from different political parties receiving donation”.
- The Ministry of Finance’s affidavit in the top court had dismissed the Election Commission’s version that the invisibility afforded to benefactors was a “retrogade step” and would wreck transparency in political funding.
Way Forward:
- One of the most critical functions of an independent judiciary in a functioning democracy is to referee the fundamentals of the democratic process.
- Governments derive their legitimacy from elections, and it is elections that grant governments the mandate to pursue their policy goals, without undue interference from courts.
- However, for just that reason, it is of vital importance that the process that leads up to the formation of the Government be policed with particular vigilance, as any taint at that stage will taint all that follows. In other words, the electoral legitimacy of the Government is questionable if the electoral process has become questionable.
- And since the Government itself cannot — in good faith — regulate the process that it itself is subject to every five years, the courts remain the only independent body that can adequately umpire and enforce the ground rules of democracy.
-Source: The Hindu
The Rising Tensions in the Balkans
Context:
The U.S. imposed fresh sanctions on Bosnian Serb leader Milorad Dodik and officials linked to him. The sanctions were imposed after Serbian ultra-nationalists, led by Dodik, initiated moves to withdraw the Serbian dominated region from the multi-ethnic institutions of Bosnia.
Relevance:
GS II- International Relations
Dimensions of the article:
- Background
- Who is Milorad Dodik?
- What has triggered the latest round of escalating tensions?
- What could be the consequences of Dodik’s agenda?
- What has been the response of the international community so far?
Background:
Earlier this month, the U.S. imposed fresh sanctions, including asset freezes and visa bans, on Bosnian Serb leader Milorad Dodik and officials linked to him. The sanctions come on the heels of rising tensions in Bosnia after Serbian ultra-nationalists, led by Dodik, resorted to hate speech against Bosnia Muslims and initiated moves to withdraw the Serbian-dominated region from institutions of the Bosnian state.
Who is Milorad Dodik?
- The Bosnian war following the break-up of Yugoslavia — which killed 1,00,000 people and displaced 2.2 million — came to an end with the signing of the Dayton Agreement in November 1995.
- As per this accord, Bosnia-Herzegovina, or Bosnia, as the state is informally called, was divided into two semi-autonomous units: the Serbian-majority Republika Srpska, and the Federation of Bosnia and Herzegovia, which is dominated by Bosniak Muslims and Catholic Croats.
- The Presidency of Bosnia is jointly held by three members, a Croat, a Bosniak and a Serb, with the Chair rotating between the three.
- Dodik is currently the Serb member of the Presidency. He was also the president of Republika Srpska from 2010 to 2018.
- Initially considered a moderate face of Serbia nationalism, he has taken an ultra-nationalist stance, making headlines for denying the Srebenica genocide, hate speech against Bosnian Muslims, and seeking to withdrawing Srpska from multi-ethnic federal institutions such as the army and judiciary. Dodik has also been accused of corruption, and pushing lucrative deals benefiting his family members.
- Critics believe that his turn to ultra-nationalism is aimed at turning attention away from personal corruption.
What has triggered the latest round of escalating tensions?
- As per the framework of the Dayton accord, Bosnia has a High Representative (HR), an international official vested with special powers to ensure the implementation of the Dayton accord and preserve peace in the region.
- In July 2021, the then High Representative Valentin Inzko, in the last week of his tenure, imposed a new law that made denying the Srebenica genocide a crime punishable by a jail term of up to five years.
- Such a law had long been debated, but could not be passed due to the veto power exercised by the Serbian member of the Presidency.
- But now that it was a reality, the Serbs were outraged. Dodik began fanning this outrage with provocative speeches, stressing time and again that the Srebenica genocide of 8,000 Bosnian Muslims was a “fabrication”.
What could be the consequences of Dodik’s agenda?
- Dodik has said that he and Serbian officials will no longer heed the orders of the High Representative.
- This constitutes a a violation of the Dayton agreement —the bamboo frame holding up a fragile peace in the region.
- He has also vowed to build exclusively Serbian institutions, including an army.
- This has alarmed many observers, who have pointed out that the creation of ‘mono-ethnic’ institutions in a multi-ethnic society, especially when accompanied by hate speech, is an early pointer to the danger of ethnic cleansing and genocide.
- If Dodik has his way, and goes ahead, it could trigger a civil war that would massively destabilise the region.
- It would also reopen old wounds in a population that has barely recovered from the trauma of the Bosnian war that ended in 1995.
What has been the response of the international community so far?
- The U.S. has been more proactive in responding to the developments, as evidenced by the sanctions it has imposed against Dodik.
- The European Union, on the other hand, has been slow to respond. The fact that any sanctions that it might seek to impose would need the assent of all the 27 member states makes it more difficult for the EU to act.
What next?
- While Dodik has denied that he wants the Serbian unit of Bosnia to secede, his rhetoric indicates otherwise. Until recently, the carrot of EU membership gave Europe some leverage over Bosnia, and the warring ethnicities had a reason to stay invested in a unified state.
- But lately, the EU has been visibly cool to the idea of adding new members from the Balkans, and with the dream of EU membership receding, politicians such as Dodik— he is not the only one —have turned to ultra-nationalism as the easiest route to popularity and power.
- Unless the U.S. and the EU act in concert to put out the fires of Serbian ultra-nationalism, the Balkans could once again go up in flames.
-Source: The Hindu
Pegasus Spyware
Context:
Israel’s Justice Minister pledged a full investigation into allegations that the controversial Pegasus spyware was used on Israeli citizens, including people who led protests against former premier Benjamin Netanyahu.
Relevance:
GS-III: Internal Security Challenges (Basics of Cyber Security; Role of media and social-networking sites in internal security challenges; Internal security challenges through communication networks), GS-II: Polity and Constitution (Constitutional Provisions, Fundamental Rights, Important Judgements)
Dimensions of the Article:
- About the Pegasus Project
- How dangerously compromising is Pegasus?
- What is a spyware and what are other similar types of Cyber Attacks?
- Pegasus in the news in the past
- About the Pegasus Attacks in India
About the Pegasus Project
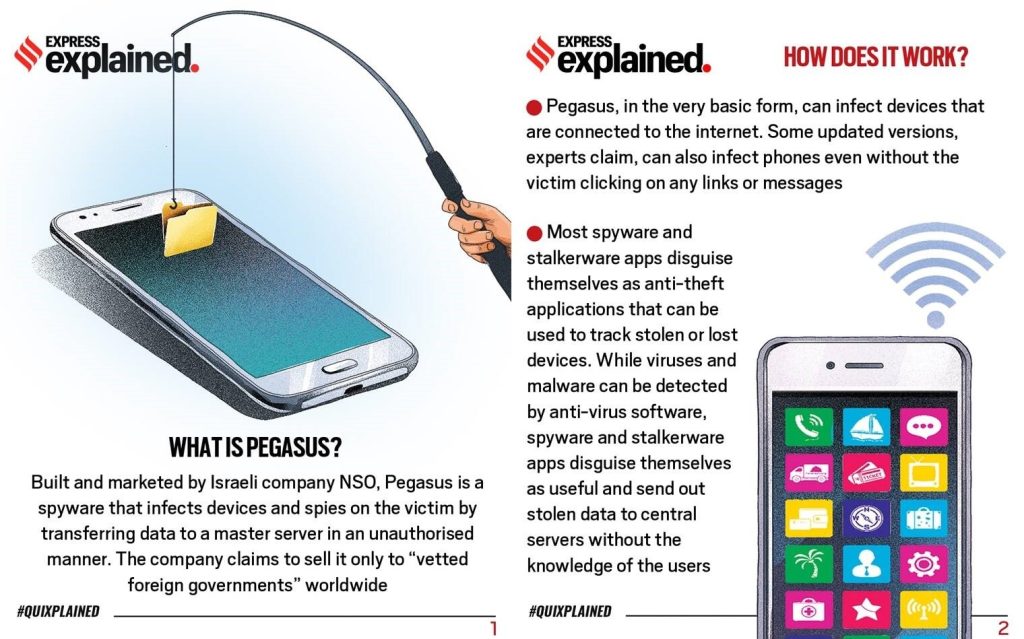
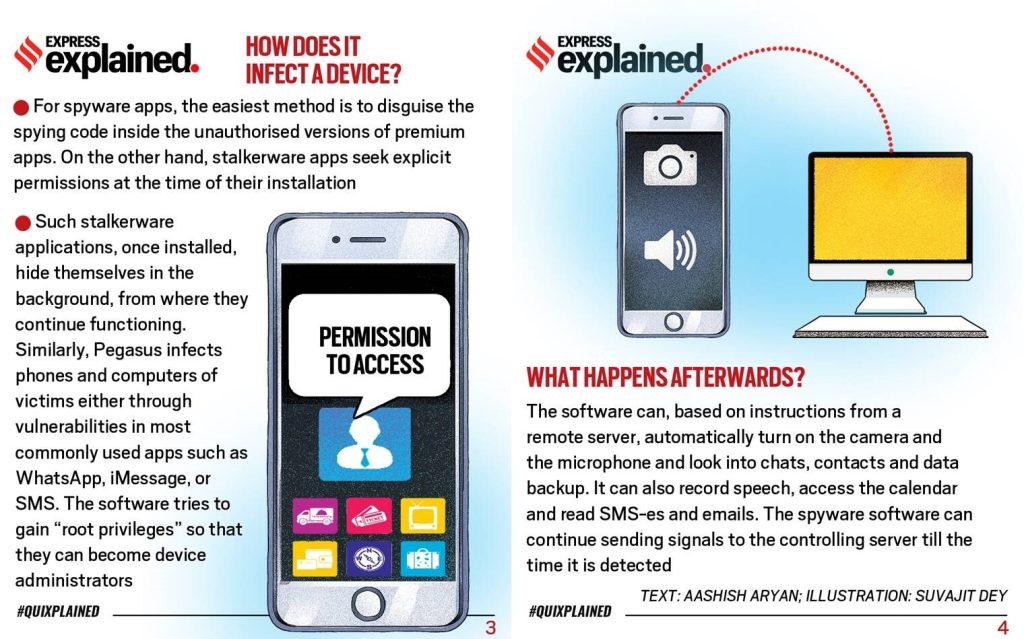
- Pegasus is a type of malicious software or malware classified as a spyware that enables law enforcement and intelligence agencies to remotely and covertly extract” data “from virtually any mobile devices”
- Pegasus is designed to gain access to devices, without the knowledge of users, and gather personal information and relay it back to whoever it is that is using the software to spy.
- A zero-click attack helps spyware like Pegasus gain control over a device without human interaction or human error. Pegasus can infect a device without the target’s engagement or knowledge. So, all awareness about how to avoid a phishing attack or which links not to click are pointless.
- Pegasus was developed by the Israeli firm NSO Group that was set up in 2010 and since then NSO’s attack capabilities have become more advanced.
How dangerously compromising is Pegasus?
- Upon installation, Pegasus contacts the attacker’s command and control (C&C) servers to receive and execute instructions and send back the target’s private data, including passwords, contact lists, calendar events, text messages, and live voice calls (even those via end-to-end-encrypted messaging apps).
- The attacker can control the phone’s camera and microphone, and use the GPS function to track a target.
- To avoid extensive bandwidth consumption that may alert a target, Pegasus sends only scheduled updates to a C&C server.
- The spyware is designed to evade forensic analysis, avoid detection by anti-virus software, and can be deactivated and removed by the attacker, when and if necessary.
What is a spyware and what are other similar types of Cyber Attacks?
What is Malware?
- Malware is short for malicious software and it is a catch-all term for various malicious software, including viruses, adware, spyware, browser hijacking software, and fake security software.
- Ransomware, Spyware, Worms, viruses, and Trojans are all varieties of malware.
Types of Malware
- Viruses which are the most commonly-known form of malware and potentially the most destructive. They can do anything from erasing the data on your computer to hijacking your computer to attack other systems, send spam, or host and share illegal content.
- Worm is a type of malware that spreads copies of itself from computer to computer which can replicate itself without any human interaction, and it does not need to attach itself to a software program in order to cause damage.
- Trojan is a type of malware that is often disguised as legitimate software which can be employed by cyber-thieves and hackers trying to gain access to users’ systems.
- Spyware collects your personal information and passes it on to interested third parties without your knowledge or consent. Spyware is also known for installing Trojan viruses.
- Ransomware is malware that employs encryption to hold a victim’s information at ransom.
- Adware displays pop-up advertisements when you are online.
- Fake security software poses as legitimate software to trick you into opening your system to further infection, providing personal information, or paying for unnecessary or even damaging “clean ups”.
- Browser hijacking software changes your browser settings (such as your home page and toolbars), displays pop-up ads and creates new desktop shortcuts. It can also relay your personal preferences to interested third parties.
Pegasus in the news in the past
- The earliest version of Pegasus discovered, which was captured by researchers in 2016, infected phones through what is called spear-phishing – text messages or emails that trick a target into clicking on a malicious link.
- In 2019, WhatsApp blamed the NSO Group for exploiting a vulnerability in its video-calling feature which secretly transmitted malicious code in an effort to infect the victim’s phone with spyware without the person even having to answer the call.
- In 2020, a Citizen Lab report flagged how government operatives used Pegasus to hack 37 phones belonging to journalists, producers, anchors, and executives at Al Jazeera and London-based Al Araby TV
About the Pegasus Attacks in India
- Human Rights activists, journalists and lawyers around the world have been targeted with phone malware sold to authoritarian governments by an Israeli surveillance firm.
- Indian ministers, government officials and opposition leaders also figure in the list of people whose phones may have been compromised by the spyware.
- Indian politicians and journalists, several Delhi-based diplomats, employees of international NGOs like the Bill and Melinda Gates Foundation etc., have been reported to be present in the list of those targeted by the Pegasus Spyware.
- The Indian government has denied any wrong doing or carrying out any unauthorised surveillance, but has not confirmed or denied whether it has purchased or deployed Pegasus spyware.
-Source: The Hindu
Economic Recovery Is Yet To Attain Durability, says ICRA
Context
Rating agency ICRA said while there was some evidence of the economic recovery becoming broad-based in the third quarter of fiscal 2022, it was yet to attain the durability being sought by the Monetary Policy Committee as a precursor to policy transmission.
- The agency expects real GDP to expand 6-6.5% year-on-year in the third quarter (8.4% in Q2 FY2022).
Relevance:
GS-III: Indian Economy (Growth and Development of Indian Economy)
Dimensions of the Article:
- Economic Recovery
- Types of Shape of Economic Recovery
Economic Recovery
- Economic Recovery is the business cycle stage following a recession that is characterized by a sustained period of improving business activity.
- Normally, during an economic recovery, GDP grows, incomes rise, and unemployment falls and as the economy rebounds.
- Economic recovery can take many forms, which is depicted using alphabetic notations. For example, a Z-shaped recovery, V-shaped recovery, U-shaped recovery, elongated U-shaped recovery, W-shaped recovery, L-shaped recovery and K-shaped recovery.
Types of Shape of Economic Recovery
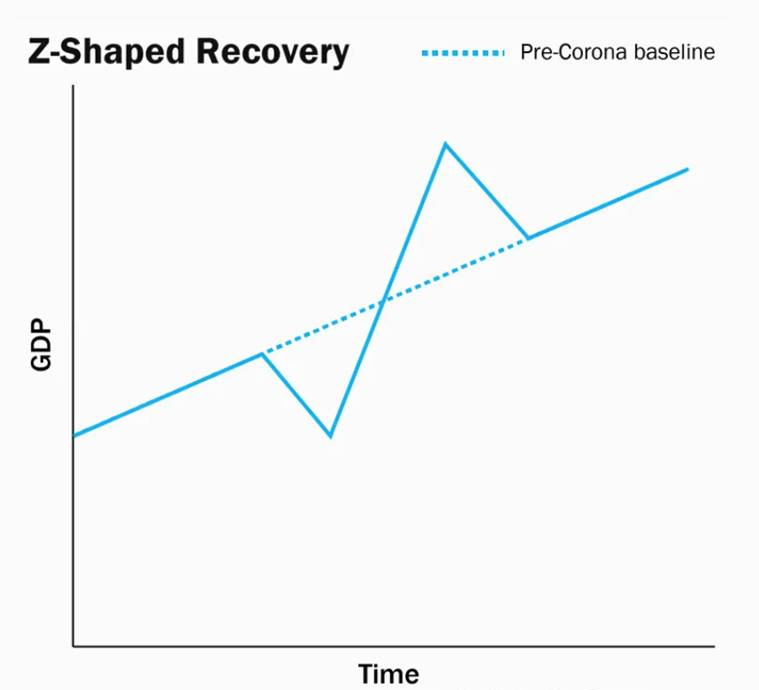
Z-shaped recovery:
- The Z-shaped recovery is the most-optimistic scenario in which the economy quickly rises like a phoenix after a crash.
- It more than makes up for lost ground (think revenge-buying after the lockdowns are lifted) before settling back to the normal trend-line, thus forming a Z-shaped chart.
- In this economic disruption lasts for a small period
- In this more than people’s incomes, it is their ability to spend is restricted.
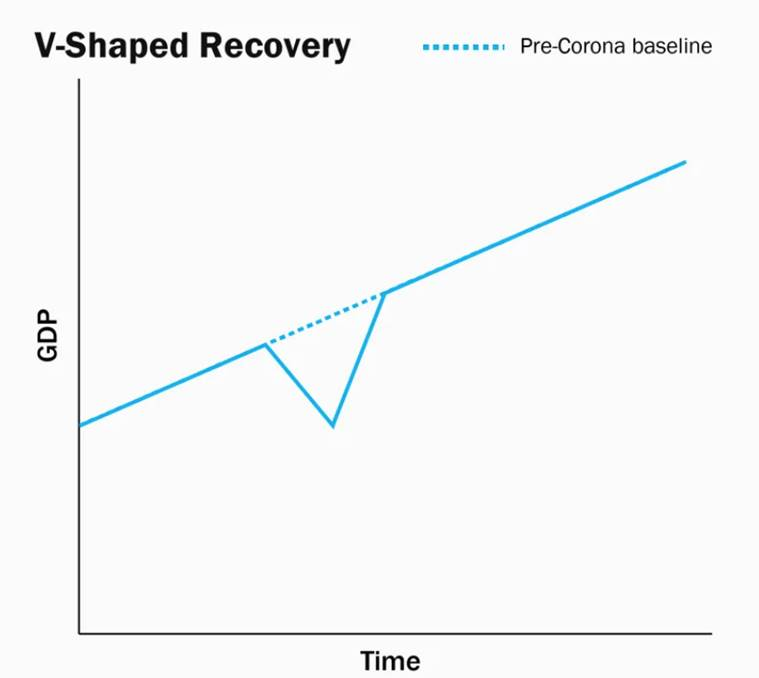
V-shaped recovery
- V-shaped recovery is a type of economic recession and recovery that resembles a “V” shape in charting.
- Specifically, a V-shaped recovery represents the shape of a chart of economic measures economists create when examining recessions and recoveries.
- A V-shaped recovery involves a sharp rise back to a previous peak after a sharp decline in these metrics.
- It is the next-best scenario after Z-shaped recovery in which the economy quickly recoups lost ground and gets back to the normal growth trend-line.
- In this, incomes and jobs are not permanently lost, and the economic growth recovers sharply and returns to the path it was following before the disruption.
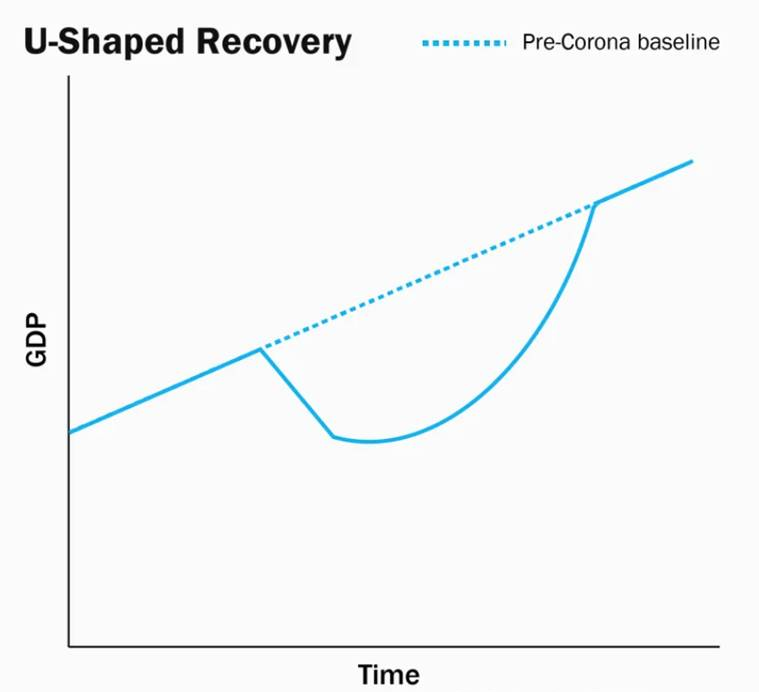
U-shaped recovery:
- A U-shaped recovery describes a type of economic recession and recovery that charts a U shape, established when certain metrics, such as employment, GDP, and industrial output sharply decline and then remain depressed typically over a period of 12 to 24 months before they bounce back again.
- In this case several jobs are lost and people fall upon their savings.
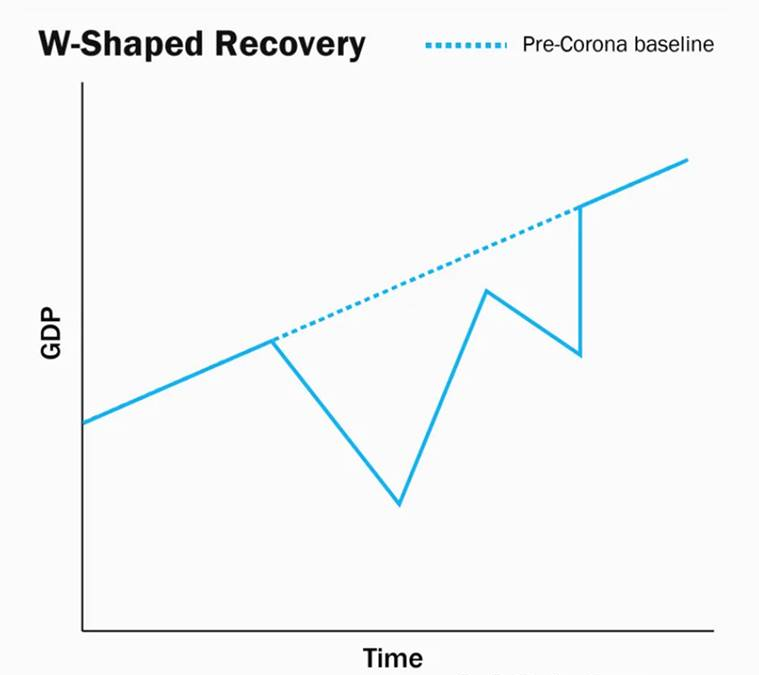
W-shaped recovery:
- A W-shaped recovery is when an economy passes through a recession into recovery and then immediately turns down into another recession.
- W-shaped recessions can be particularly painful because the brief recovery that occurs can trick investors into getting back in too early.
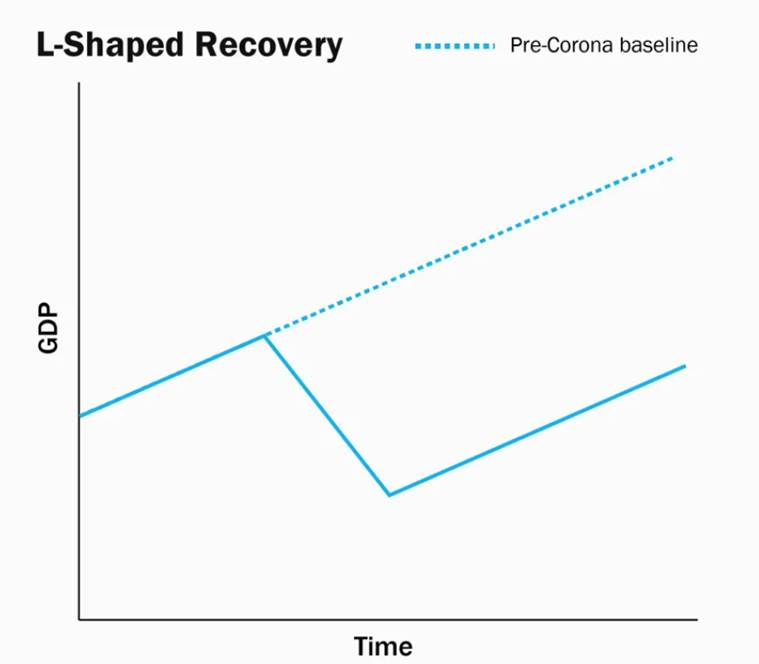
L-shaped recovery:
- An L-shaped recovery is when, after a steep recession, the economy experiences a slow rate of recovery, which resembles the shape of the letter “L” when charted as a line graph.
- L-shaped recoveries are characterized by persistently high unemployment, a slow return of business investment activity, and a sluggish rate of growth in economic output, and are associated with some of the worst economic episodes through history.
-Source: The Hindu
Silver Line project
Context:
Amid mounting protests from Opposition parties and organisations in Kerala, the BJP-led government at the Centre is weighing its options before giving a green signal to the SilverLine project of the Kerala Rail Development Corporation Limited (K-Rail).
Relevance:
GS III- Infrastructure
Dimensions of the article:
- About Silver Line Project
- Expected Benefits of SilverLine Project
About Silver Line Project
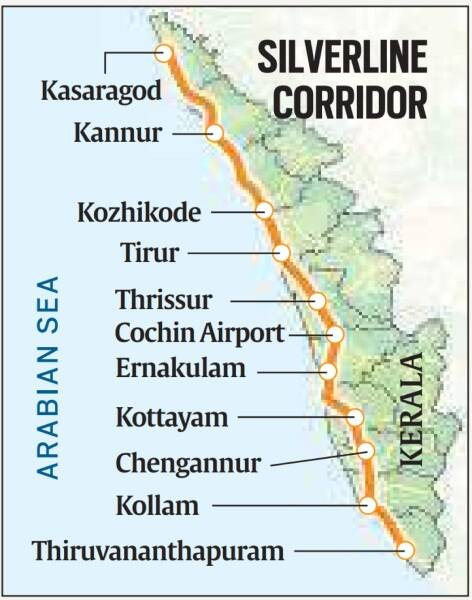
- It is a 532-km semi-high speed rail corridor.
- It will connect 11 of the 14 districts of Kerala, situated at both ends. Alappuzha, Wayanad, and Idukki are not part of this.
- Aim: It will cut the travel time between the two ends of the state from 12 hours to less than four hours.
- It also plans to connect the corridor with the international airports at Kochi and Thiruvananthapuram.
- The plan for a high-speed rail network was first suggested in the 2011 Budget.
- The project deadline is 2025.
Expected Benefits of SilverLine Project:
- Reduce greenhouse gas emissions
- Help in expansion of Ro-Ro services
- Produce employment opportunities
- Integrate airports and IT corridors and
- Faster development of cities it passes through.
-Source: The Hindu
Miss Kerala
Context:
A section of aquarists and ornamental fish breeders are surprised that the Denison barb (Miss Kerala), a native freshwater fish species commonly found in parts of Karnataka and Kerala, has been included in Schedule I of the Wild Life Protection Act, 1982 (amendment bill).
Relevance:
GS III- Conservation, Environmental Pollution & Degradation, Species in News
Dimensions of this article:
- About Miss Kerala
- Why included in Schedule I of WPA?
About Miss Kerala

- Miss Kerala is also known as Denison barb, red-line torpedo barb and roseline shark.
- Its scientific name is Sahyadria denisonii.
- The fish is featured with red and black stripes on its body.
- It is found in the States of Kerala and Karnataka.
- It has been listed on the IUCN Redlist as Vulnerable, in 2010.
- This species is known to inhabit fast-flowing hill streams and is often found in rocky pools with thick vegetation along river banks.
Why included in Schedule I of WPA?
- Ironically, its beauty is the biggest threat to its survival, as it is highly sought-after in the international aquarium trade, constituting 60 – 65% of the total live ornamental fish exported from India.
- Its numbers are also decreasing owing to habitat degradation due to deforestation, mining, agriculture, urban expansion and hydro-electric projects.
-Source: The Hindu
Swamp Deer
Context:
The population of the vulnerable eastern swamp deer, extinct elsewhere in South Asia, has dipped (from 907 in 2018 to 868 in 2020 ) in the Kaziranga National Park and Tiger Reserve.
Relevance:
GS III- Conservation, Environmental Pollution & Degradation, Species in News
Dimensions of this article:
- About Swamp Deer
- Why included in Schedule I of WPA?
About Swamp Deer
- The swamp deer also called as barasingha is a deer species distributed in the Indian subcontinent.
- Populations in northern and central India are fragmented, and two isolated populations occur in southwestern Nepal.
- It has been locally extinct in Pakistan and Bangladesh, and its presence is uncertain in Bhutan.
- Swamp deers do occur in the Kanha National Park of Madhya Pradesh, in two localities in Assam, and in only 6 localities in Uttar Pradesh.
Conservation status
- IUCN Red List: Endangered
- CITES: Appendix I
- Wildlife Protection Act of 1972: Schedule I
Kaziranga National Park
- Kaziranga National Park is a national park in the Golaghat, Karbi Anglong and Nagaon districts of the state of Assam.
- It is a World Heritage Site and hosts two-thirds of the world’s great one-horned rhinoceroses.
- Kaziranga is recognized as an Important Bird Area by BirdLife International for conservation of avifaunal species.
- Along with the iconic Greater one-horned rhinoceros, the park is the breeding ground of elephants, wild water buffalo, and swamp deer.
- Over the time, the tiger population has also increased in Kaziranga, and that’s the reason why Kaziranga was declared as Tiger Reserve in 2006.
- Due to the difference in altitude between the eastern and western areas of the park, here one can see mainly four types of vegetation’ like alluvial inundated grasslands, alluvial savanna woodlands, tropical moist mixed deciduous forests, and tropical semi-evergreen forests.
- Kaziranga is a vast expanse of tall elephant grass, marshland, and dense tropical moist broadleaf forests, criss-crossed by four major rivers, including the Brahmaputra, and the park includes numerous small bodies of water.
- Kaziranga has flat expanses of fertile, alluvial soil, formed by erosion and silt deposition by the River Brahmaputra.
- The history of Kaziranga as a protected area can be traced back to 1904 when the wife of the Viceroy of India, Lord Curzon visited the area and persuaded to take measures to protect rhinoceros in the area.
-Source: The Hindu




